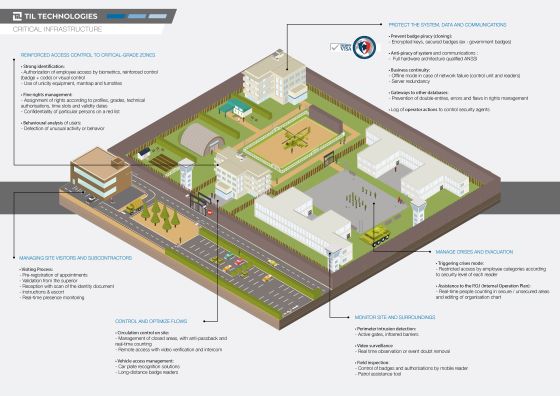
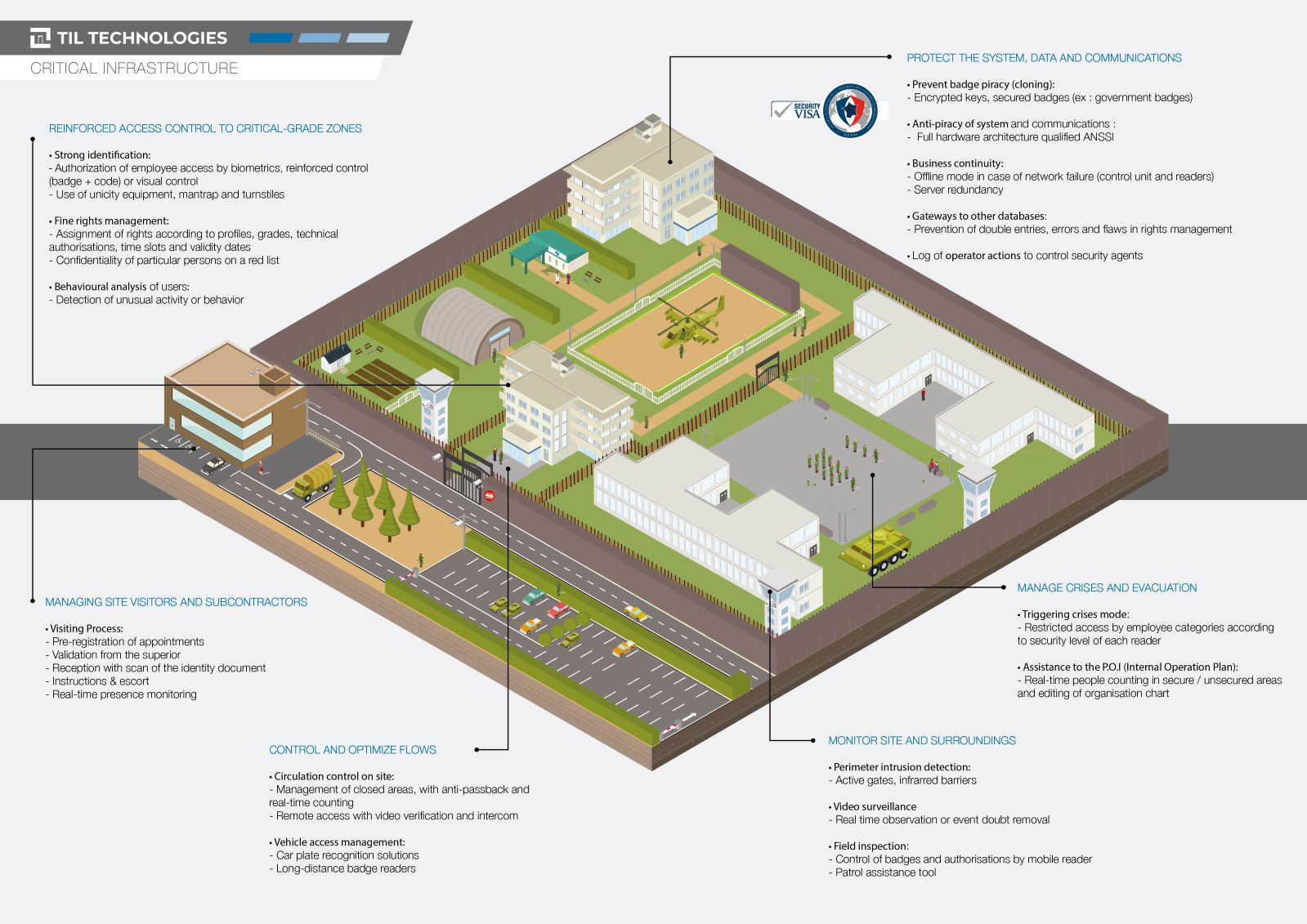
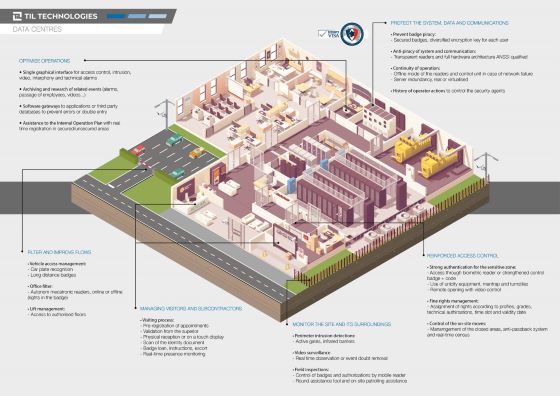
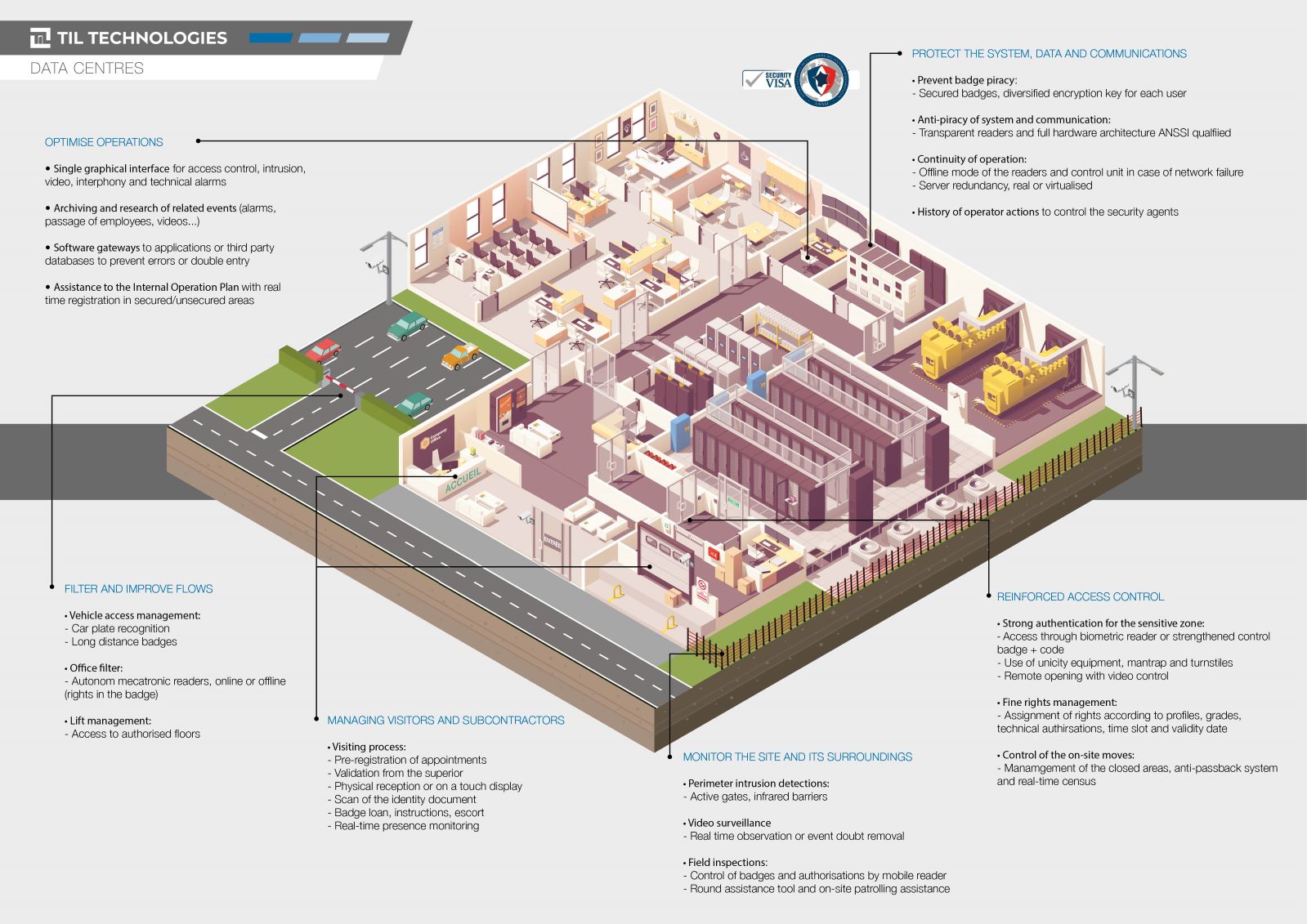
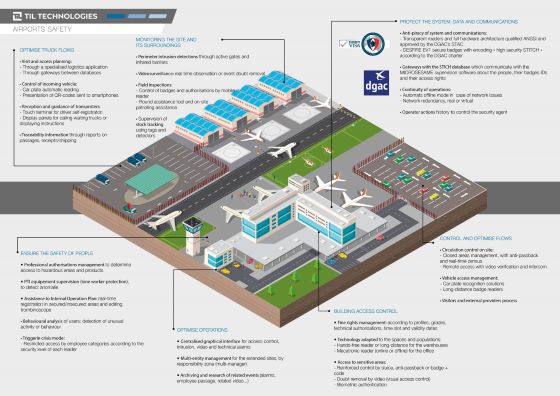
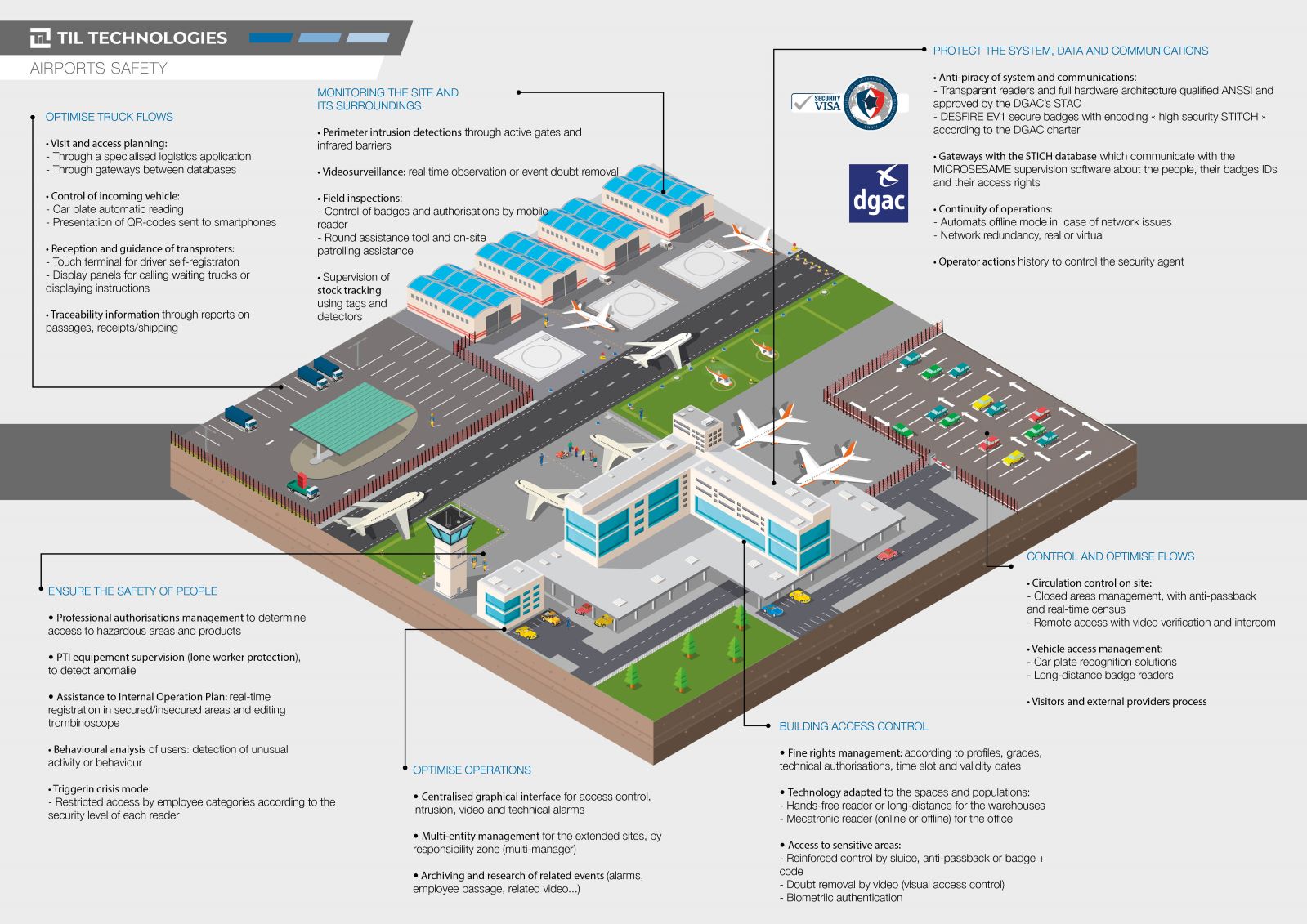
Whether to isolate inmates, control access to important weapons and equipment, or protect confidential information, datacenters and strategic command areas, sensitive sites all require enhanced security measures.
Faced with the risks of piracy, espionage, sabotage or evasion, impermeability must be ensured by strong authentication solutions (Biometrics, dual identification, video control, etc.) and security (encryption, security keys, etc.).
Through its software and hardware solutions, TIL TECHNOLOGIES can meet all your high-security needs.